linux下ARM64栈分析
| 软件版本 | 硬件版本 | 更新内容 |
|---|---|---|
| linux 5.8.18 | arm64 |
1.重要问题
1.1 压栈操作是怎么完成的?
在我们写高级语言程序时,其实不需要关心压栈的操作,因为你的函数调用会被编译器编译,会产生一些压栈的指令,由 这些指令来进行压栈操作,返回时会进行出栈操作。
1.2 那些东西会入栈?
以下内容(如果有的话)按顺序依次入栈:
- 在调用子函数时多于8个的参数时,会压栈通过栈来传递参数
- 在函数中定义的局部变量会入栈
- 在函数的起始也就是1.4时提到的prologue中会将x0~x7传过来的参数压栈
- 如果在子函数内部又调用了子子函数会将FP和LR压栈,否则只保留在x29和x30寄存器中
所以最终一个栈帧的样子如下: 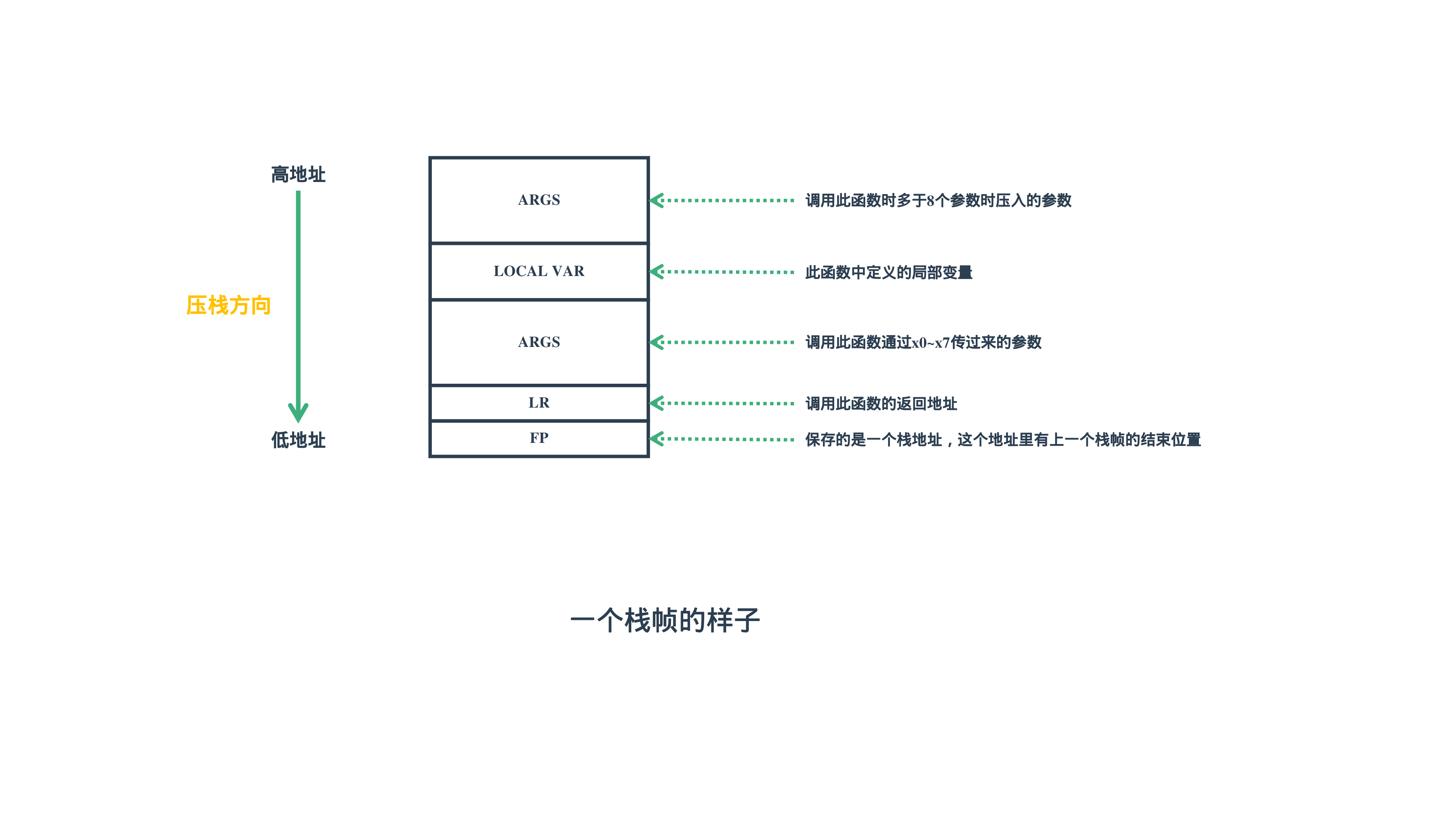
1.3 可否手动操作栈数据?
可以,通过像操作通过寄存器一样操作sp就可以,如sub sp, sp, #16
1.4 在内核arch/arm64/kernel/stacktrace.c中有如下代码,注释部分如何理解?
/*
* AArch64 PCS assigns the frame pointer to x29.
*
* A simple function prologue looks like this:
* sub sp, sp, #0x10
* stp x29, x30, [sp]
* mov x29, sp
*
* A simple function epilogue looks like this:
* mov sp, x29
* ldp x29, x30, [sp]
* add sp, sp, #0x10
*/
/*
* Unwind from one frame record (A) to the next frame record (B).
*
* We terminate early if the location of B indicates a malformed chain of frame
* records (e.g. a cycle), determined based on the location and fp value of A
* and the location (but not the fp value) of B.
*/
int notrace unwind_frame(struct task_struct *tsk, struct stackframe *frame)
{
...
}
prologue,其实是用来保存sp中FP,LR到x29和x30,这样在函数调用完成时才能正确的返回。尤其是x30就是返回地址。在函数 调用时,会将返回地址LR和FP压栈,那在进入函数时会首先调用x30值,用于在函数执行完成可以正确返回。 prologue,其实是恢复到sp中,因为返回时会由cpu自动执行出栈操作,所以需要先将sp指向调用进来的时的位置,这样出栈之 后才是正确的sp位置。
1.5 dump_stack打印信息解析
[63233.623158] Call trace:
[63233.623172] dump_backtrace+0x0/0x1c0
[63233.623177] show_stack+0x24/0x30
[63233.623182] dump_stack+0xa0/0xd8
[63233.623187] write_version+0x9c/0xc8
[63233.623192] proc_reg_write+0x80/0xc0
[63233.623196] __vfs_write+0x60/0x160
[63233.623199] vfs_write+0xac/0x1b0
[63233.623202] SyS_write+0x74/0xf0
[63233.623205] el0_svc_naked+0x34/0x38
每行打印就是一个调用过程中函数,打印格式为:函数名+调用下一个函数地方的下一条指令相对函数起始地址的偏移/函数的结束地址相对起始地址的偏移(也可以理解函数长度) 例如:
[63233.623177] show_stack+0x24/0x30
ffffff800808e000 <show_stack>:
ffffff800808e000: a9be7bfd stp x29, x30, [sp, #-32]!
ffffff800808e004: 910003fd mov x29, sp
ffffff800808e008: f9000bf3 str x19, [sp, #16]
ffffff800808e00c: aa0003f3 mov x19, x0
ffffff800808e010: aa1e03e0 mov x0, x30
ffffff800808e014: 940037e4 bl ffffff800809bfa4 <_mcount>
ffffff800808e018: aa1303e1 mov x1, x19
ffffff800808e01c: d2800000 mov x0, #0x0 // #0
ffffff800808e020: 97ffff18 bl ffffff800808dc80 <dump_backtrace>
ffffff800808e024: f9400bf3 ldr x19, [sp, #16]
ffffff800808e028: a8c27bfd ldp x29, x30, [sp], #32
ffffff800808e02c: d65f03c0 ret
ffffff800808e030 <die>:
ffffff800808e030: a9bc7bfd stp x29, x30, [sp, #-64]!
ffffff800808e034: 910003fd mov x29, sp
ffffff800808e038: a90153f3 stp x19, x20, [sp, #16]
函数起始地址:ffffff800808e000, 调用发生在ffffff800808e020,那么下一条指令就在ffffff800808e024,这个地址相对函数起始地址偏移0x24,结束地址 相对于起始地址偏移为0x30。
2. 使用crash加-t获取栈信息
crash> bt ffffffc76005ba00 -t
PID: 15453 TASK: ffffffc76005ba00 CPU: 3 COMMAND: "bash"
START: __switch_to at ffffff8008086f08
[ffffff801726b738] __schedule at ffffff8008e83aec
[ffffff801726b758] schedule at ffffff8008e840a8
[ffffff801726b7b8] rt_spin_unlock at ffffff8008e884e0
[ffffff801726b7e8] schedule_hrtimeout_range_clock at ffffff8008e87584
[ffffff801726b808] schedule_hrtimeout_range at ffffff8008e875c8
[ffffff801726b838] add_wait_queue at ffffff80081060f4
[ffffff801726b858] pty_write_room at ffffff800877cc2c
[ffffff801726b878] tty_write_room at ffffff8008775204
[ffffff801726b898] poll_schedule_timeout at ffffff80082a757c
[ffffff801726b8b8] tty_poll at ffffff800876d4d4
[ffffff801726b8c8] do_select at ffffff80082a7ee8
[ffffff801726b918] core_sys_select at ffffff80082a8b98
[ffffff801726ba58] pollwake at ffffff80082a78e8
[ffffff801726ba98] pollwake at ffffff80082a78e8
[ffffff801726bae8] rt_spin_unlock at ffffff8008e884dc
[ffffff801726bb18] tty_set_termios at ffffff80087757c4
[ffffff801726bb28] insert_work at ffffff80080d2f34
[ffffff801726bb38] rt_spin_unlock at ffffff8008e884e0
[ffffff801726bb48] rt_spin_unlock at ffffff8008e884dc
[ffffff801726bb68] queue_work_on at ffffff80080d4c8c
[ffffff801726bb98] rt_spin_unlock at ffffff8008e884e0
[ffffff801726bbb8] queue_work_on at ffffff80080d4c88
[ffffff801726bbc8] rt_spin_unlock at ffffff8008e884dc
[ffffff801726bbd8] rt_spin_unlock at ffffff8008e884dc
[ffffff801726bc08] __wake_up_common_lock at ffffff800810639c
[ffffff801726bc18] rt_spin_unlock at ffffff8008e884e0
[ffffff801726bc28] __check_object_size at ffffff80082854ec
[ffffff801726bc48] core_sys_select at ffffff80082a8a58
[ffffff801726bc88] sys_pselect6 at ffffff80082a9228
[ffffff801726bd68] vfs_write at ffffff800828d0a8
[ffffff801726bdb8] vfs_write at ffffff800828d08c
[ffffff801726bdc8] sigprocmask at ffffff80080c80d4
[ffffff801726bde8] sys_pselect6 at ffffff80082a9210
[ffffff801726be28] el0_svc_naked at ffffff8008084180
这个at后面的地址是LR返回地址,例如:
START: __switch_to at ffffff8008086f08
crash> dis ffffff8008086f08
0xffffff8008086f08 <__switch_to+240>: ldp x19, x20, [sp,#16]
3. 使用crash获取栈信息
crash> bt ffffffc76005ba00
PID: 15453 TASK: ffffffc76005ba00 CPU: 3 COMMAND: "bash"
#0 [ffffff801726b730] __switch_to at ffffff8008086f04
#1 [ffffff801726b750] __schedule at ffffff8008e83ae8
#2 [ffffff801726b7e0] schedule at ffffff8008e840a4
#3 [ffffff801726b800] schedule_hrtimeout_range_clock at ffffff8008e87580
#4 [ffffff801726b890] schedule_hrtimeout_range at ffffff8008e875c4
#5 [ffffff801726b8c0] poll_schedule_timeout at ffffff80082a7578
#6 [ffffff801726b910] do_select at ffffff80082a7ee4
#7 [ffffff801726bc80] core_sys_select at ffffff80082a8b94
#8 [ffffff801726be20] sys_pselect6 at ffffff80082a9224
#9 [ffffff801726bff0] el0_svc_naked at ffffff800808417c
PC: 0000007f9136c360 LR: 000000556aec8834 SP: 0000007fd00aab10
X29: 0000007fd00aab10 X28: 0000007fd00aac78 X27: 0000000000000000
X26: 0000007fd00aabf7 X25: 000000556af01000 X24: 000000556af0e000
X23: 0000000000000001 X22: 000000556af0ddc8 X21: 0000000000000000
X20: 0000000000000001 X19: 0000007f913f5000 X18: 0000007f913f6a70
X17: 0000007f9136c2f8 X16: 000000556af00af8 X15: 0000000000000000
X14: 000000000000001f X13: 202361696469766e X12: 0000000000000020
X11: 7f7f7f7f7f7f7f7f X10: 1f2260686368756d X9: 000000556af306a0
X8: 0000000000000048 X7: 0000000000000000 X6: 0000007f913fb270
X5: 0000007fd00aab78 X4: 0000000000000000 X3: 0000000000000000
X2: 0000000000000000 X1: 0000007fd00aac78 X0: 0000000000000001
ORIG_X0: 0000000000000001 SYSCALLNO: 48 PSTATE: 60000000
这个at前面的是函数名,后面是这个函数执行到的那个指令的地址,也就是说在函数执行到at后面的那个指令时发生跳转.例如:
#0 [ffffff801726b730] __switch_to at ffffff8008086f04
crash> dis ffffff8008086f04
0xffffff8008086f04 <__switch_to+236>: bl 0xffffff8008085b3c <cpu_switch_to>
4. 手动通过内存来解析栈
正常运行时,进程的栈结构如下图所示: 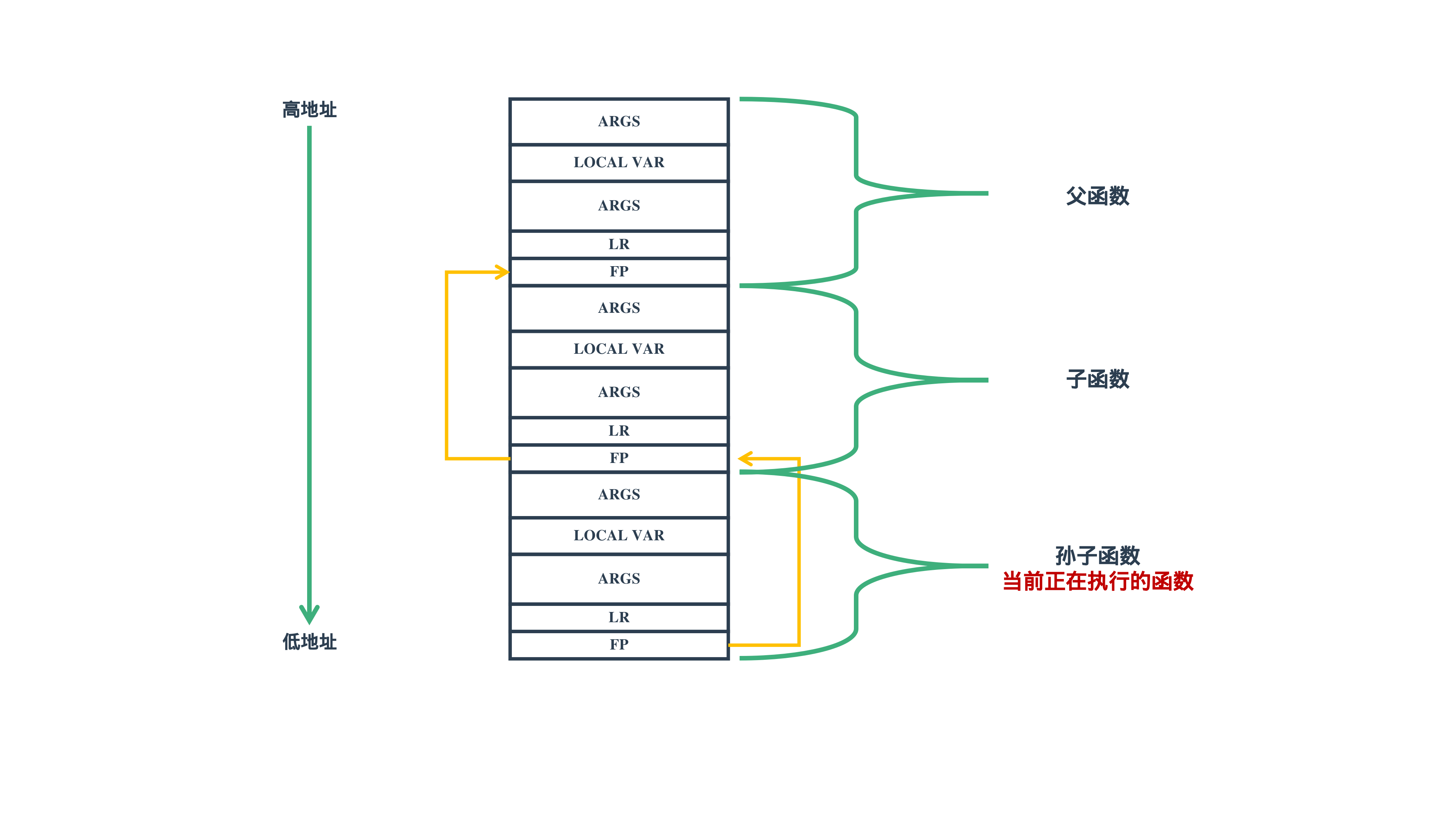
以ffffffc76005ba00这个进程来分析,先通过struct来获取该进程的task_struct信息如下:
crash> task_struct ffffffc76005ba00
struct task_struct {
...
stack = 0xffffff8017268000,
...
thread = {
cpu_context = {
x19 = 18446743830518442880,
x20 = 18446743830507403776,
x21 = 0,
x22 = 18446743524111015936,
x23 = 18446743524115927040,
x24 = 18446743830428584960,
x25 = 18446743830507405312,
x26 = 18446743831112684480,
x27 = 18446743524103176360,
x28 = 18446743830507403776,
fp = 18446743524342150960,
sp = 18446743524342150960,
pc = 18446743524088508168
},
tp_value = 547898296064,
tp2_value = 0,
fpsimd_state = {
{
user_fpsimd = {
vregs = {0, 0x00000000000001610000000000000000, 0x000000556af14010000000556af242a0, 0xa800a800aaa0aaaaa800a800aaa0aaaa, 0x80200800000000008020080000000000, 0, 0, 0x80200802802008028020080280200802, 0, 0, 0, 0, 0, 0, 0, 0, 0x40100401401004014010040140100401, 0xfd00fd00fcfefcfcfd00fd00fcfefcfc, 0x00100001001000010010000100100001, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0},
fpsr = 0,
fpcr = 0,
__reserved = {0, 0}
},
{
vregs = {0, 0x00000000000001610000000000000000, 0x000000556af14010000000556af242a0, 0xa800a800aaa0aaaaa800a800aaa0aaaa, 0x80200800000000008020080000000000, 0, 0, 0x80200802802008028020080280200802, 0, 0, 0, 0, 0, 0, 0, 0, 0x40100401401004014010040140100401, 0xfd00fd00fcfefcfcfd00fd00fcfefcfc, 0x00100001001000010010000100100001, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0},
fpsr = 0,
fpcr = 0
}
},
cpu = 3
},
fault_address = 0,
fault_code = 0,
debug = {
suspended_step = 0,
bps_disabled = 0,
wps_disabled = 0,
hbp_break = {0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0},
hbp_watch = {0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0}
}
}
}
从上面可以stack的起始地址为0xffffff8017268000,在arm平台栈大小为16K,也就是结束地址为0xffffff801726c000.
通过下面的crash指令来dump从栈顶0xffffff801726b730开始的内存数据: 从bt的输出可以看到最上FP是0xffffff801726b730,但是栈顶的地址应该是比这个小,因为调用了别的函数又有压栈操作,所以 从0xffffff801726b700打印,我们打印2048个四字 这里有一个细节,从0xffffff801726b700开始打2048个四字,不会直的打印这么多,超出0xffffff801726c000将不再打印
以下就是通过dis来分析栈的过程,主要是解析FP和LR信息来解析出调用的过程。起始为0xffffff801726b730.也就每个FP位置
crash> gdb x/2048xg 0xffffff801726b700
---------------------------------------------------------------------------------------------------------------
0xffffff801726b700: 0xffffff8008e988c0 0xffffff80095fe000
---------------------------------------------------------------------------------------------------------------
0xffffff801726b710: 0xffffff801726b730 0xffffff8008086ea4
crash> dis 0xffffff801726b730
dis: WARNING: ffffff801726b730: no associated kernel symbol found
0xffffff801726b730: b 0xffffff8013c19470
crash> dis 0xffffff8013c19470
dis: WARNING: ffffff8013c19470: no associated kernel symbol found
0xffffff8013c19470: dis: seek error: kernel virtual address: ffffff8013c19470 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c19470
crash> dis 0xffffff8008086ea4
0xffffff8008086ea4 <__switch_to+140>: ldr w0, [x19,#60]
---------------------------------------------------------------------------------------------------------------
0xffffff801726b720: 0xffffffc760ae2b80 0xffffffc76005ba00
---------------------------------------------------------------------------------------------------------------
0xffffff801726b730: 0xffffff801726b750 0xffffff8008e83aec
crash> dis 0xffffff801726b750
dis: WARNING: ffffff801726b750: no associated kernel symbol found
0xffffff801726b750: b 0xffffff8013c196d0
crash> dis 0xffffff8013c196d0
dis: WARNING: ffffff8013c196d0: no associated kernel symbol found
0xffffff8013c196d0: dis: seek error: kernel virtual address: ffffff8013c196d0 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c196d0
crash> dis 0xffffff8008e83aec
0xffffff8008e83aec <__schedule+660>: bl 0xffffff80080e86e0 <finish_task_switch>
---------------------------------------------------------------------------------------------------------------
0xffffff801726b740: 0xffffffc7841993c0 0xffffffc760ae2b80
---------------------------------------------------------------------------------------------------------------
0xffffff801726b750: 0xffffff801726b7e0 0xffffff8008e840a8
crash> dis 0xffffff801726b7e0
dis: WARNING: ffffff801726b7e0: no associated kernel symbol found
0xffffff801726b7e0: b 0xffffff8013c197e0
crash> dis 0xffffff8013c197e0
dis: WARNING: ffffff8013c197e0: no associated kernel symbol found
0xffffff8013c197e0: dis: seek error: kernel virtual address: ffffff8013c197e0 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c197e0
crash> dis 0xffffff8008e840a8
0xffffff8008e840a8 <schedule+72>: ldr w0, [x19,#24]
---------------------------------------------------------------------------------------------------------------
0xffffff801726b760: 0xffffffc76005ba00 0xffffffc76005ba00
0xffffff801726b770: 0x0000000000000000 0x0000000000000000
0xffffff801726b780: 0x0000000000000001 0x0000000000000104
0xffffff801726b790: 0x0000000000000008 0x0000000000000000
0xffffff801726b7a0: 0x0000000000000001 0x0000000000000000
0xffffff801726b7b0: 0xffffff801726b7d0 0xffffff8008e884e0
0xffffff801726b7c0: 0xffffffc760908000 0x10e1d1482375e500
0xffffff801726b7d0: 0xffffff8000000004 0x10e1d1482375e500
---------------------------------------------------------------------------------------------------------------
0xffffff801726b7e0: 0xffffff801726b800 0xffffff8008e87584
crash> dis 0xffffff801726b800
dis: WARNING: ffffff801726b800: no associated kernel symbol found
0xffffff801726b800: b 0xffffff8013c19a40
crash> dis 0xffffff8013c19a40
dis: WARNING: ffffff8013c19a40: no associated kernel symbol found
0xffffff8013c19a40: dis: seek error: kernel virtual address: ffffff8013c19a40 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c19a40
crash> dis 0xffffff8008e87584
0xffffff8008e87584 <schedule_hrtimeout_range_clock+244>: mov w0, #0xfffffffc // #-4
---------------------------------------------------------------------------------------------------------------
0xffffff801726b7f0: 0xffffff8009aad000 0x0000000000000000
---------------------------------------------------------------------------------------------------------------
0xffffff801726b800: 0xffffff801726b890 0xffffff8008e875c8
crash> dis 0xffffff801726b890
dis: WARNING: ffffff801726b890: no associated kernel symbol found
0xffffff801726b890: b 0xffffff8013c19b90
crash> dis 0xffffff8013c19b90
dis: WARNING: ffffff8013c19b90: no associated kernel symbol found
0xffffff8013c19b90: dis: seek error: kernel virtual address: ffffff8013c19b90 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c19b90
crash> dis 0xffffff8008e875c8
0xffffff8008e875c8 <schedule_hrtimeout_range+56>: ldr x21, [sp,#32]
---------------------------------------------------------------------------------------------------------------
0xffffff801726b810: 0x0000000000000000 0x0000000000000000
0xffffff801726b820: 0x0000000000000000 0x0000000000000000
0xffffff801726b830: 0x0000000000000000 0xffffff80081060f4
0xffffff801726b840: 0xffffff801726baa0 0xffffff801726ba88
0xffffff801726b850: 0xffffff801726b870 0xffffff800877cc2c
0xffffff801726b860: 0xffffffc757567000 0xffffffc750df1800
0xffffff801726b870: 0xffffff801726b890 0xffffff8008775204
0xffffff801726b880: 0xffffffc757567000 0x10e1d1482375e500
---------------------------------------------------------------------------------------------------------------
0xffffff801726b890: 0xffffff801726b8c0 0xffffff80082a757c
crash> dis 0xffffff801726b8c0
dis: WARNING: ffffff801726b8c0: no associated kernel symbol found
0xffffff801726b8c0: b 0xffffff8013c19d00
crash> dis 0xffffff8013c19d00
dis: WARNING: ffffff8013c19d00: no associated kernel symbol found
0xffffff8013c19d00: dis: seek error: kernel virtual address: ffffff8013c19d00 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c19d00
crash> dis 0xffffff80082a757c
0xffffff80082a757c <poll_schedule_timeout+100>: mrs x1, sp_el0
---------------------------------------------------------------------------------------------------------------
0xffffff801726b8a0: 0xffffff8009aad000 0x0000000000000001
0xffffff801726b8b0: 0xffffff801726ba08 0xffffff800876d4d4
---------------------------------------------------------------------------------------------------------------
0xffffff801726b8c0: 0xffffff801726b910 0xffffff80082a7ee8
dis: WARNING: ffffff801726b910: no associated kernel symbol found
0xffffff801726b910: b 0xffffff8013c1ab10
crash> dis 0xffffff8013c1ab10
dis: WARNING: ffffff8013c1ab10: no associated kernel symbol found
0xffffff8013c1ab10: dis: seek error: kernel virtual address: ffffff8013c1ab10 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c1ab10
crash> dis 0xffffff80082a7ee8
0xffffff80082a7ee8 <do_select+944>: cmp w0, #0x0
---------------------------------------------------------------------------------------------------------------
0xffffff801726b8d0: 0x0000000000000001 0x0000000000000000
0xffffff801726b8e0: 0x0000000000000001 0x0000000000000001
0xffffff801726b8f0: 0x0000000000000000 0x0000000000000000
0xffffff801726b900: 0x0000000000000001 0x10e1d1482375e500
---------------------------------------------------------------------------------------------------------------
0xffffff801726b910: 0xffffff801726bc80 0xffffff80082a8b98
crash> dis 0xffffff801726bc80
dis: WARNING: ffffff801726bc80: no associated kernel symbol found
0xffffff801726bc80: b 0xffffff8013c1b500
crash> dis 0xffffff8013c1b500
dis: WARNING: ffffff8013c1b500: no associated kernel symbol found
0xffffff8013c1b500: dis: seek error: kernel virtual address: ffffff8013c1b500 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c1b500
crash> dis 0xffffff80082a8b98
0xffffff80082a8b98 <core_sys_select+520>: mov w20, w0
---------------------------------------------------------------------------------------------------------------
0xffffff801726b920: 0x0000000000000008 0x0000000000000001
0xffffff801726b930: 0xffffff8009aad000 0x0000007fd00aac78
0xffffff801726b940: 0x0000000000000000 0x0000000000000000
0xffffff801726b950: 0x0000000000000000 0xffffff801726bd18
0xffffff801726b960: 0xffffff801726bd18 0xffffff801726bd28
0xffffff801726b970: 0x0000000000000000 0x0000000000000000
0xffffff801726b980: 0x0000000000000000 0xffffff801726bd40
0xffffff801726b990: 0xffffff801726bd38 0xffffff801726bd30
0xffffff801726b9a0: 0x0000000000000000 0xffffff801726bce8
0xffffff801726b9b0: 0x0000000000000000 0xffffff801726bd28
0xffffff801726b9c0: 0xffffff801726bd20 0xffffff801726bd18
0xffffff801726b9d0: 0x0000000000000001 0x0000000000000000
0xffffff801726b9e0: 0x0000000000000000 0x0000000000000000
0xffffff801726b9f0: 0x0000000000000000 0x0000000100000000
0xffffff801726ba00: 0xffffffc78416d3c0 0x0000000000000000
0xffffff801726ba10: 0x00000000000000db 0x0000000000000000
0xffffff801726ba20: 0xffffffc76005ba00 0x0000000000000000
0xffffff801726ba30: 0xffffffc700000002 0xffffffc750df1800
0xffffff801726ba40: 0x00000000000000db 0xffffff8000000000
0xffffff801726ba50: 0xffffff801726ba08 0xffffff80082a78e8
0xffffff801726ba60: 0xffffffc7575672f8 0xffffffc7575672f8
0xffffff801726ba70: 0xffffffc7575672c8 0xffffffc750df1800
0xffffff801726ba80: 0x00000000000000db 0xffffff8000000000
0xffffff801726ba90: 0xffffff801726ba08 0xffffff80082a78e8
0xffffff801726baa0: 0xffffffc7575672b8 0xffffffc7575672b8
0xffffff801726bab0: 0xffffffc757567288 0xffffff8009aae010
0xffffff801726bac0: 0x0000000000000003 0x0000000000000040
0xffffff801726bad0: 0xffffffc760908000 0xffffff8017249000
0xffffff801726bae0: 0xffffff801726bb50 0xffffff8008e884dc
0xffffff801726baf0: 0xffffffc760908000 0xffffffc751342208
0xffffff801726bb00: 0x0000000000000027 0x0000000000000000
0xffffff801726bb10: 0xffffffc760908000 0xffffff80087757c4
0xffffff801726bb20: 0xffffff801726bb40 0xffffff80080d2f34
0xffffff801726bb30: 0xffffff801726bb50 0xffffff8008e884e0
0xffffff801726bb40: 0xffffff801726bbb0 0xffffff8008e884dc
0xffffff801726bb50: 0xffffffc78418fc18 0x0000000000000001
0xffffff801726bb60: 0xffffff801726bbd0 0xffffff80080d4c8c
0xffffff801726bb70: 0xffffff80095ff000 0x0000000000000001
0xffffff801726bb80: 0xffffffc76005ba00 0xffffffc751342208
0xffffff801726bb90: 0xffffff801726bbb0 0xffffff8008e884e0
0xffffff801726bba0: 0xffffffc78418fc18 0x10e1d1482375e500
0xffffff801726bbb0: 0xffffff801726bbd0 0xffffff80080d4c88
0xffffff801726bbc0: 0xffffff801726bc30 0xffffff8008e884dc
0xffffff801726bbd0: 0xffffff801726bc40 0xffffff8008e884dc
0xffffff801726bbe0: 0xffffffc757567288 0x0000000000000001
0xffffff801726bbf0: 0x0000000000000001 0x0000000000000000
0xffffff801726bc00: 0xffffff801726bc60 0xffffff800810639c
0xffffff801726bc10: 0xffffff801726bc30 0xffffff8008e884e0
0xffffff801726bc20: 0xffffff801726bc40 0xffffff80082854ec
0xffffff801726bc30: 0xffffff801726bd18 0x0000000000000008
0xffffff801726bc40: 0xffffff801726bc80 0xffffff80082a8a58
0xffffff801726bc50: 0x0000000000000008 0x0000000000000001
0xffffff801726bc60: 0xffffff8009aad000 0x0000007fd00aac78
0xffffff801726bc70: 0x0000000000000100 0x10e1d1482375e500
---------------------------------------------------------------------------------------------------------------
0xffffff801726bc80: 0xffffff801726be20 0xffffff80082a9228
crash> dis 0xffffff801726be20
dis: WARNING: ffffff801726be20: no associated kernel symbol found
0xffffff801726be20: b 0xffffff8013c1bde0
crash> dis 0xffffff8013c1bde0
dis: WARNING: ffffff8013c1bde0: no associated kernel symbol found
0xffffff8013c1bde0: dis: seek error: kernel virtual address: ffffff8013c1bde0 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c1bde0
crash> dis 0xffffff80082a9228
0xffffff80082a9228 <sys_pselect6+776>: mov w2, #0x0 // #0
---------------------------------------------------------------------------------------------------------------
0xffffff801726bc90: 0x0000000000000008 0xffffff8009aad000
0xffffff801726bca0: 0x0000000000000000 0x0000000000000001
0xffffff801726bcb0: 0x0000007fd00aac78 0x0000000000000000
0xffffff801726bcc0: 0x0000000000000000 0x0000007fd00aabf8
0xffffff801726bcd0: 0xffffffc76005ba00 0x0000000000000000
0xffffff801726bce0: 0xffffff801726bd00 0xffffff801726bd18
0xffffff801726bcf0: 0xffffff801726bd20 0xffffff801726bd28
0xffffff801726bd00: 0xffffff801726bd30 0xffffff801726bd38
0xffffff801726bd10: 0xffffff801726bd40 0x0000000000000001
0xffffff801726bd20: 0x0000000000000000 0x0000000000000000
0xffffff801726bd30: 0x0000000000000000 0x0000000000000000
0xffffff801726bd40: 0x0000000000000000 0xffffff801726beb0
0xffffff801726bd50: 0x000000556af510a0 0x0000000000000015
0xffffff801726bd60: 0xffffff801726be30 0xffffff800828d0a8
0xffffff801726bd70: 0x0000000000000002 0xffffffc750df1800
0xffffff801726bd80: 0xffffff801726be30 0xffffffc74fa60f00
0xffffff801726bd90: 0xffffffc750df1810 0x0000000000000015
0xffffff801726bda0: 0x0000000000000124 0x0000000000000040
0xffffff801726bdb0: 0xffffff8008e91000 0xffffff800828d08c
0xffffff801726bdc0: 0xffffff801726bde0 0xffffff80080c80d4
0xffffff801726bdd0: 0xffffff8009aad000 0x0000000000000002
0xffffff801726bde0: 0xffffff801726be20 0xffffff80082a9210
0xffffff801726bdf0: 0x0000000000000008 0xffffff8009aad000
0xffffff801726be00: 0x0000000000000000 0x0000000000000001
0xffffff801726be10: 0x0000000000000000 0x10e1d1482375e500
---------------------------------------------------------------------------------------------------------------
0xffffff801726be20: 0xffffff801726bff0 0xffffff8008084180
crash> dis 0xffffff801726be20
dis: WARNING: ffffff801726be20: no associated kernel symbol found
0xffffff801726be20: b 0xffffff8013c1bde0
crash> dis 0xffffff8013c1bde0
dis: WARNING: ffffff8013c1bde0: no associated kernel symbol found
0xffffff8013c1bde0: dis: seek error: kernel virtual address: ffffff8013c1bde0 type: "gdb_readmem callback"
Cannot access memory at address 0xffffff8013c1bde0
crash> dis 0xffffff8008084180
0xffffff8008084180 <el0_svc_naked+52>: b 0xffffff8008083f3c <ret_fast_syscall>
---------------------------------------------------------------------------------------------------------------
0xffffff801726be30: 0xffffffffffffff24 0x000000477ab90000
0xffffff801726be40: 0x00000000ffffffff 0x0000007f9136c360
0xffffff801726be50: 0x0000000060000000 0x0000000000000015
0xffffff801726be60: 0x0000000000000124 0x0000000000000048
0xffffff801726be70: 0xffffff8008e91000 0xffffffc76005ba00
0xffffff801726be80: 0xffffffffffffff1c 0x000000477ab90000
0xffffff801726be90: 0x00000000ffffffff 0x0000007f9136598c
0xffffff801726bea0: 0x0000000020000000 0x0000000000000000
0xffffff801726beb0: 0x0000000000000000 0x10e1d1482375e500
0xffffff801726bec0: 0x0000000000000001 0x0000007fd00aac78
0xffffff801726bed0: 0x0000000000000000 0x0000000000000000
0xffffff801726bee0: 0x0000000000000000 0x0000007fd00aab78
0xffffff801726bef0: 0x0000007f913fb270 0x0000000000000000
0xffffff801726bf00: 0x0000000000000048 0x000000556af306a0
0xffffff801726bf10: 0x1f2260686368756d 0x7f7f7f7f7f7f7f7f
0xffffff801726bf20: 0x0000000000000020 0x202361696469766e
0xffffff801726bf30: 0x000000000000001f 0x0000000000000000
0xffffff801726bf40: 0x000000556af00af8 0x0000007f9136c2f8
0xffffff801726bf50: 0x0000007f913f6a70 0x0000007f913f5000
0xffffff801726bf60: 0x0000000000000001 0x0000000000000000
0xffffff801726bf70: 0x000000556af0ddc8 0x0000000000000001
0xffffff801726bf80: 0x000000556af0e000 0x000000556af01000
0xffffff801726bf90: 0x0000007fd00aabf7 0x0000000000000000
0xffffff801726bfa0: 0x0000007fd00aac78 0x0000007fd00aab10
0xffffff801726bfb0: 0x000000556aec8834 0x0000007fd00aab10
0xffffff801726bfc0: 0x0000007f9136c360 0x0000000060000000
0xffffff801726bfd0: 0x0000000000000001 0x0000000000000048
0xffffff801726bfe0: 0x0000000000000000 0x0000000000000000
---------------------------------------------------------------------------------------------------------------
0xffffff801726bff0: 0x0000000000000000 0x0000000000000000
---------------------------------------------------------------------------------------------------------------
0xffffff801726c000: gdb: invalid kernel virtual address: ffffff801726c000 type: "gdb_readmem_callback"
提示
欢迎评论、探讨,如果发现错误请指正。转载请注明出处! 探索者
 探索者
探索者